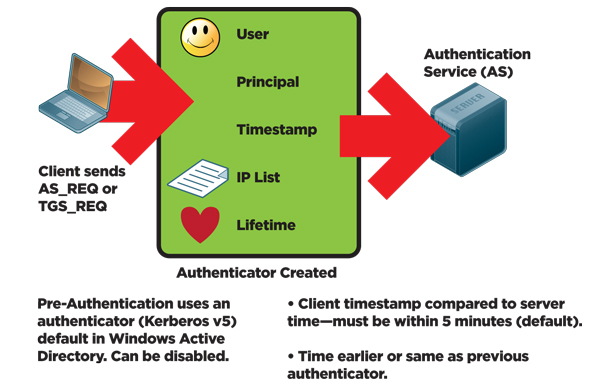
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
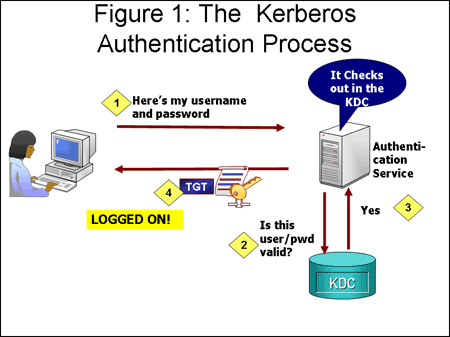
Kerberos Authentication Protocol Blog On Information Security And Other Technical Topics

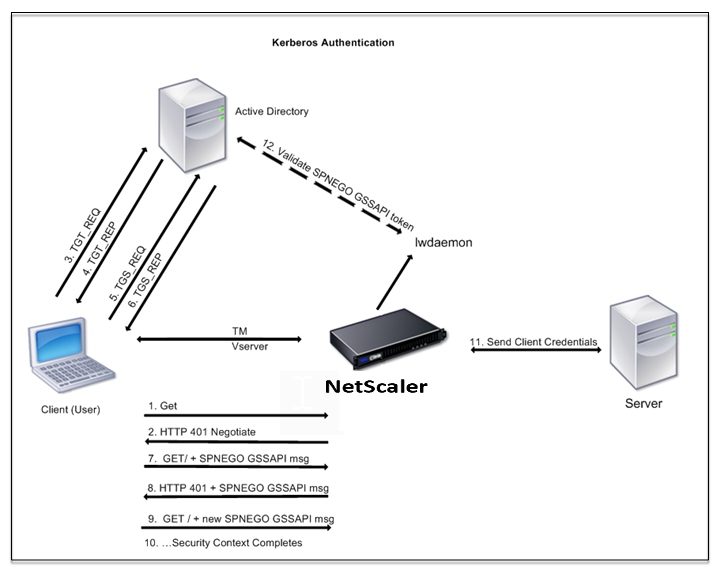
How Citrix Adc Implements Kerberos For Client Authentication
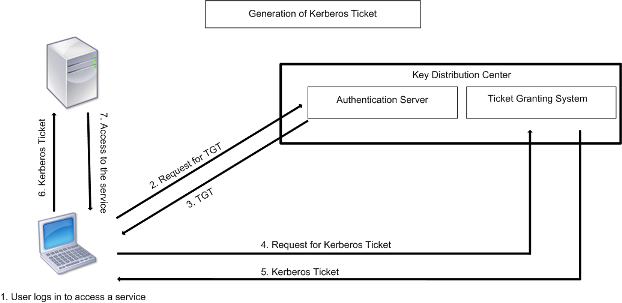
Handling Authentication Authorization And Auditing With Kerberos Ntlm
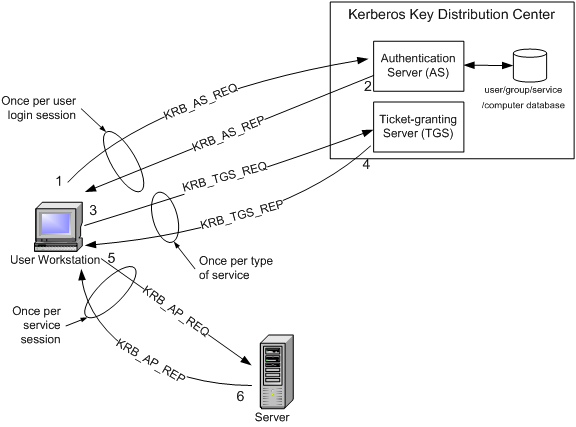
Intel Amt Sdk Implementation And Reference Guide
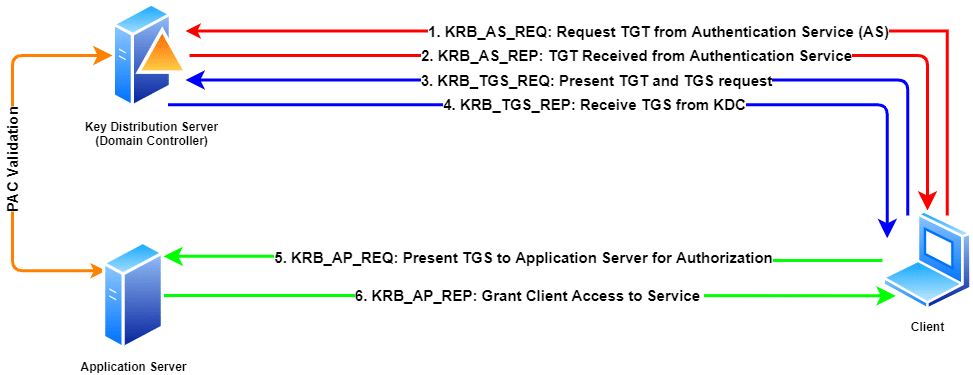
What Is Kerberos Understanding Kerberos What Is It How Does It Work
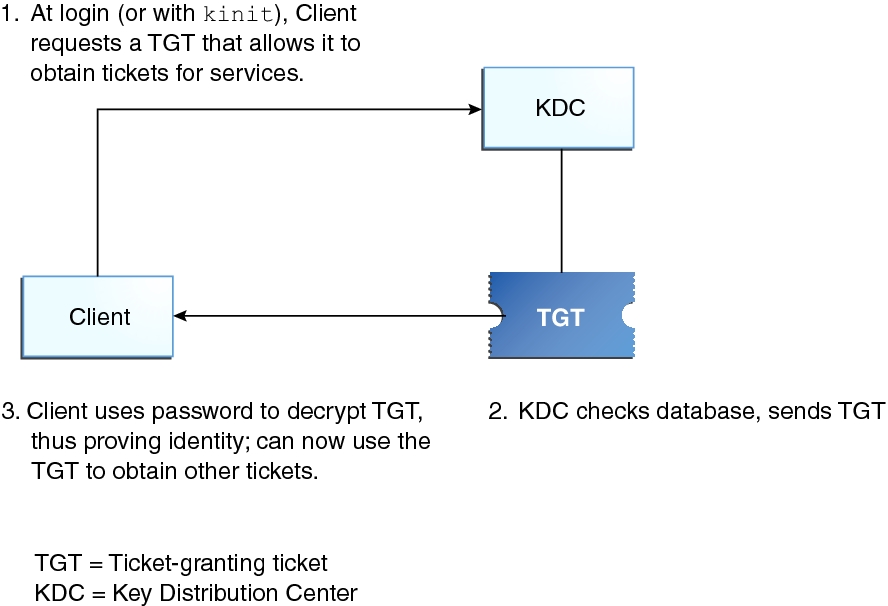
How The Kerberos Service Works Managing Kerberos And Other Authentication Services In Oracle Solaris 11 3
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com

Kerberos Authentication Process Download Scientific Diagram
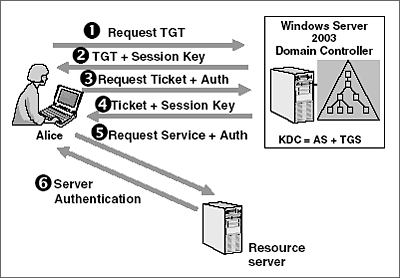
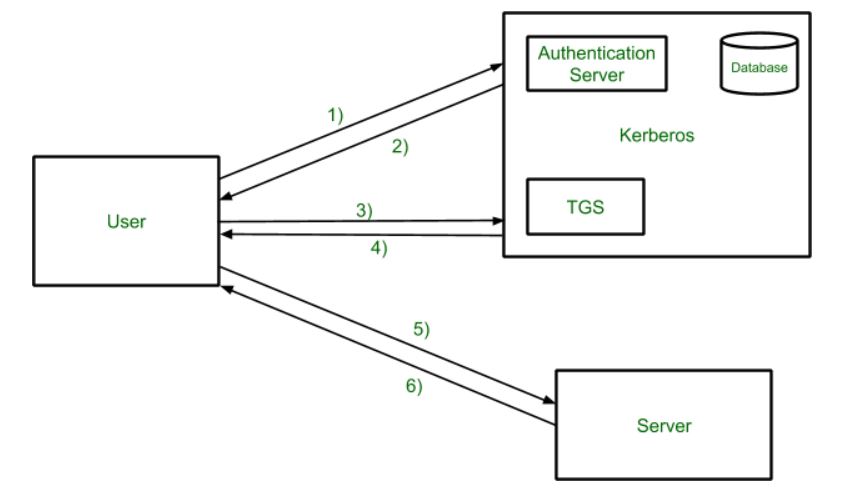
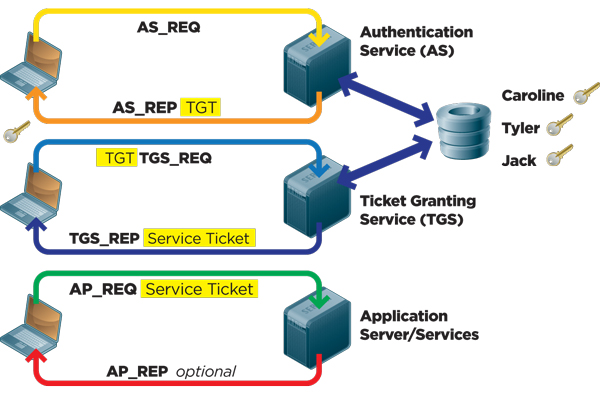
Five Steps To Using The Kerberos Protocol

The Diagram Of Kerberos Authentication Protocol Download Scientific Diagram

Kerberos Authentication Protocol Download Scientific Diagram

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
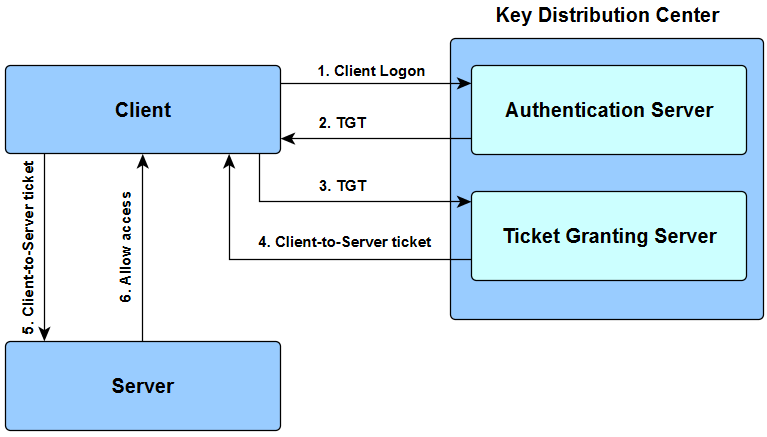
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram
Ken Schaefer Iis And Kerberos Part 1 What Is Kerberos And How Does It Work
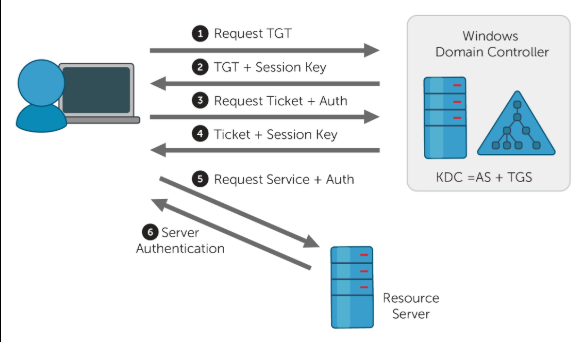
Let S Talk About Kerberos Summary By John D Cyber Jun 2021 Medium